Overview
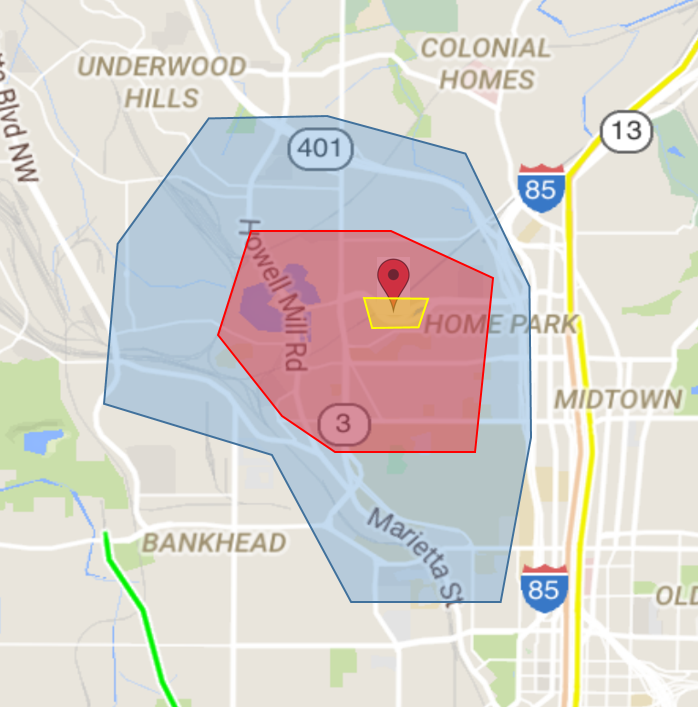
In Contrast to conventional location cloaking approaches, ReverseClock supports the following key features:
- Bidirectional Reversible Perturbation: When users with higher privilege have access to more fine granular information, the perturbed anonymized data can be de-anonymized using those credentials.
- Multilevel Privacy: ReverseCloak supports multilevel location privacy that allows different data users to infer different levels of information from the exposed location information based on their access credentials and access privilege levels entitled to them.
Motivation

Location privacy: With advances in sensing and positioning technology, fueled by the ubiquitous deployment of wireless networks, location-aware computing has become a fundamental model for offering a wide range of life enhancing services. However, the ability to locate users and mobile objects opens doors for new threats - the intrusion of location privacy.
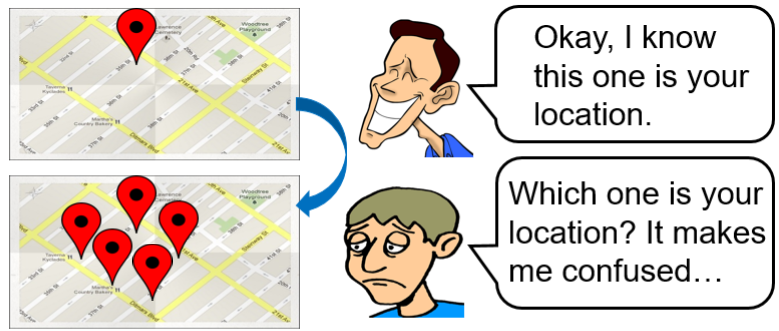
Location anonymization: Location anonymization refers to the process of perturbing user location information such that the perturbed information becomes indistinguishable from that of a set of other users.
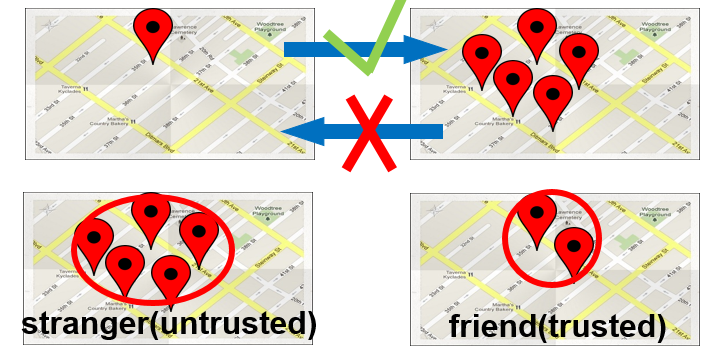
Motivations: Conventional location perturbed techniques are generally designed to be:
- Unidirectional: Accurate data cannot be recovered once the data is perturbed.
- Unilevel Protection: Both trusted and semi-trusted parties get the same anonymized data.
Algorithms
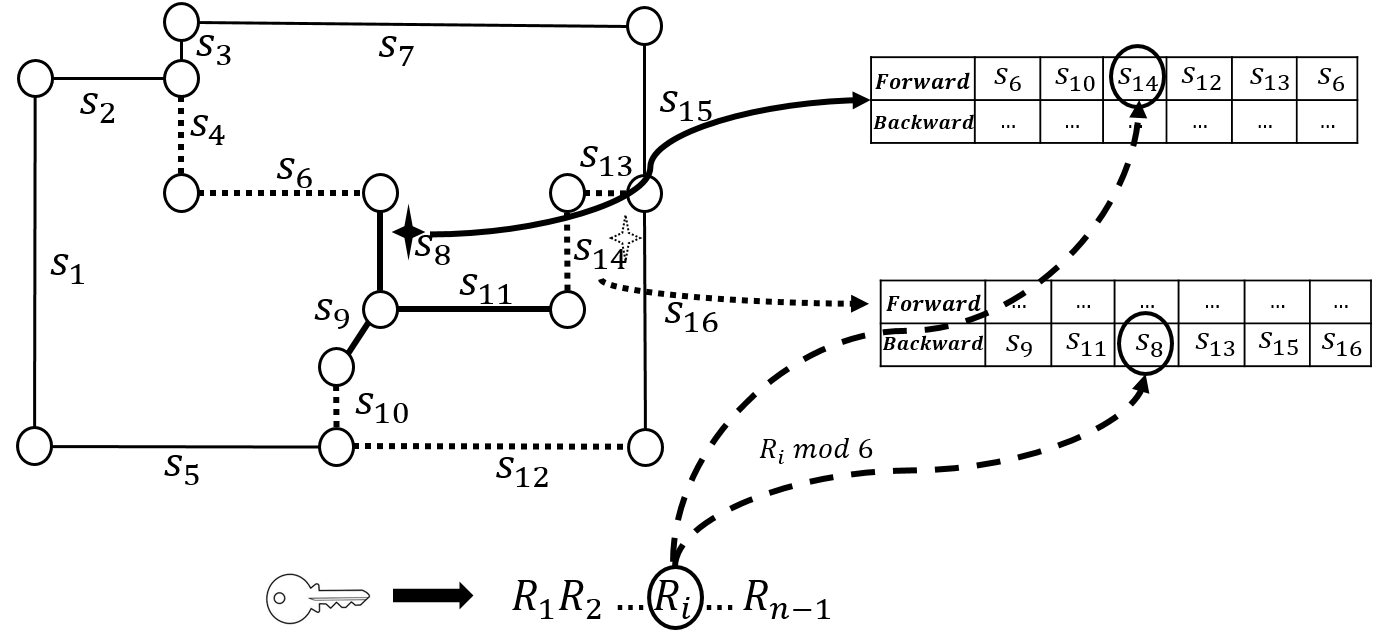
Key design challenges: ReverseCloak algorithms pick road segments in a pseudorandomly deterministic order to form cloaking regions such that the segments can be removed from the cloaking region in the reverse order when de-anonymized. A key challenge during the de-anonymization process occurs due to two forms of collisions:
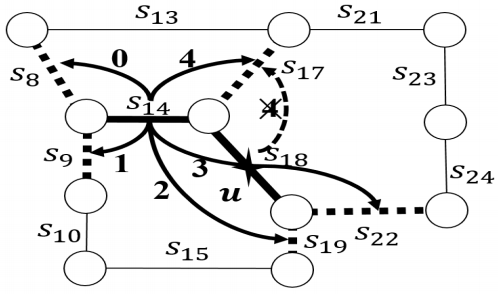
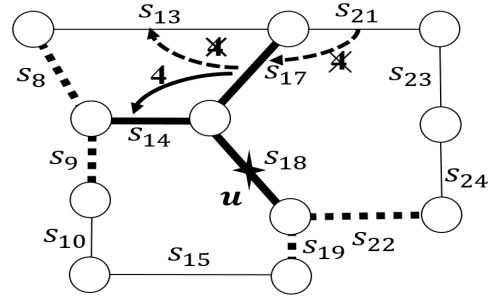
Collision-free ReverseCloak mechanisms: To handle collision challenge, ReverseCloak uses collision-free reversible cloaking mechanisms based on two approaches:
- Reversible global expansion: In the first approach, collisions are prevented by carefully assigning the transition values to the possible transitions among two sets of segments in a dynamic on-the-fly manner during anonymization.
- Reversible pre-assignment-based local expansion: In the second approach, the transitions among all the segments in the road network graph are assigned transition values.
Publications
- Chao Li and Balaji Palanisamy, "ReverseCloak: Protecting Multi-level Location Privacy over Road Networks", Proc. of 24th ACM International Conference on Information and Knowledge Management (CIKM 2015), Melbourne, Australia. [PDF]
- Chao Li and Balaji Palanisamy, "De-anonymizable Location Cloaking for Privacy-controlled Mobile Systems", Proc. of 9th International Conference on Network and System Security (NSS 2015), New York, USA.[PDF]
- Chao Li, Balaji Palanisamy, Aravind A. Kalaivanan and Sriram Raghunathan, "ReverseCloak: A Reversible Multi-level Location Privacy Protection System", Proc. of 37th IEEE International Conference on Distributed Computing Systems (ICDCS 2017), Atlanta, USA.[PDF][Demo video]